LimaCharlie is a SecOps Cloud Platform
Security operations for the modern era
Whether you’re looking for endpoint security, an observability pipeline, detection and response rules, or other underlying security capabilities, LimaCharlie’s SecOps Cloud Platform helps you build a flexible and scalable security program that can evolve as fast as threat actors.
The SecOps Cloud Platform Advantage
Gone are the days of one-size-fits-all security solutions that do not adequately address the complexities of modern networks and evolving threats. These general-purpose tools lack the flexibility to adapt to your unique environment and specific needs. As a result, organizations end up with a fragmented collection of tools that need to be manually integrated and stitched together, leading to inefficiencies, gaps in security coverage, and extreme costs.
Not anymore.
LimaCharlie’s SecOps Cloud Platform provides you with comprehensive enterprise protection that brings together critical cybersecurity capabilities and eliminates integration challenges and security gaps for more effective protection against today’s threats.
The SecOps Cloud Platform offers a unified platform where you can build customized solutions effortlessly. With open APIs, centralized telemetry, and automated detection and response mechanisms, it’s time cybersecurity moves into the modern era.
Simplifying procurement, deployment and integration of best-of-breed cybersecurity solutions, the SecOps Cloud Platform delivers complete protection tailored to each organization’s specific needs, much in the same way IT Clouds have supported enterprises for years.
Trusted by technological leaders in information security.
Enterprise Organizations
Reduce the number of vendors, get the right solutions to your specific needs and easily integrate into your environment for a fraction of the costs.
Managed Security Service Providers
A reliable, scalable way of building multi-tenant services for your customers without vendor lock-in, long contractual commitments, or high costs.
Founders & Product Builders
Prototype new products and bring them to market exponentially faster than before and scale your costs alongside your revenue linearly.
Assemble a stack that’s right for you
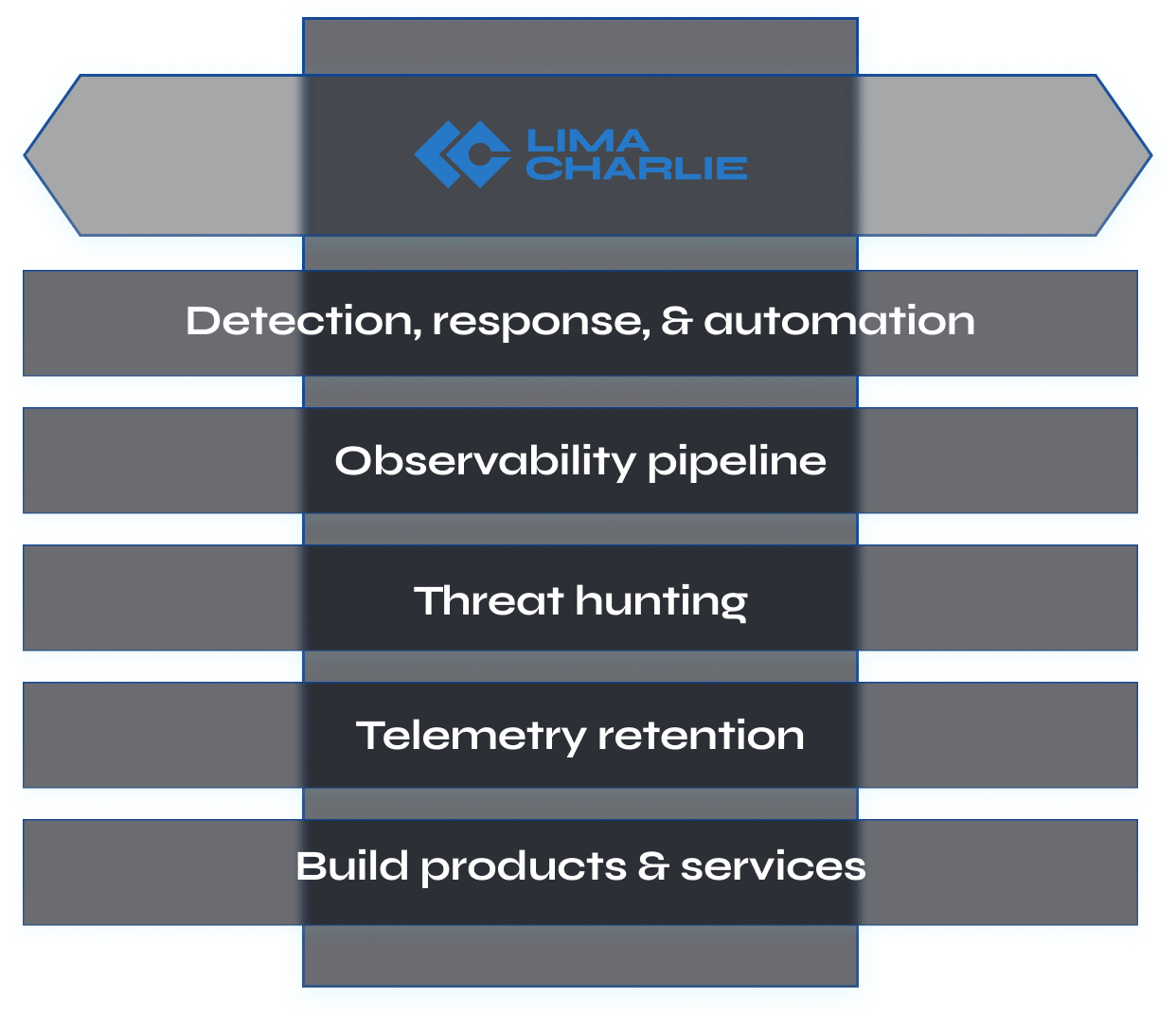
LimaCharlie delivers the core components needed to secure and monitor any given organization: things like, deploying endpoint capabilities through a single agent regardless of the technology, alerting and correlating from logs regardless of the source, automating analysis and response regardless of the environment.

Jonathan Haas
Lead SecOps, Carta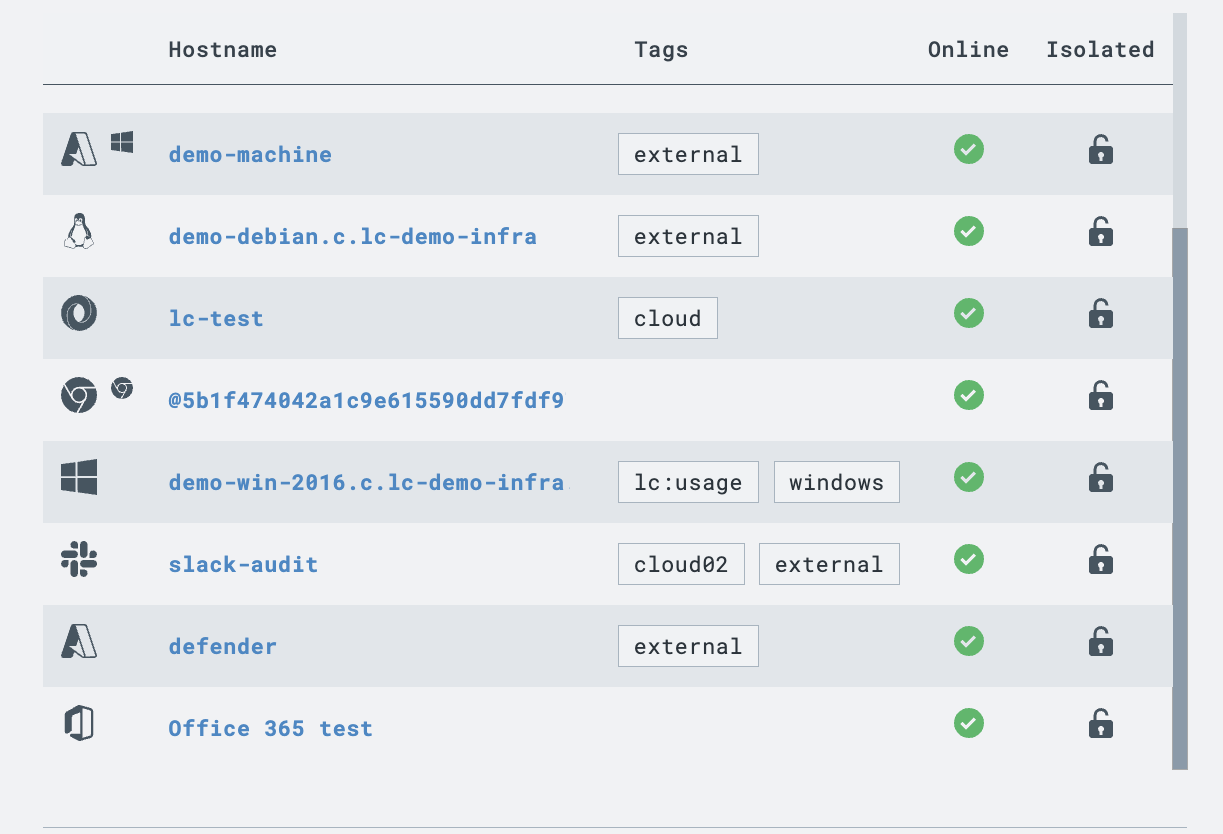
Integrate with your existing security stack
Unify external log, telemetry, and tools to gain the context and insights you need to operationalize security into a single UI at scale. LimaCharlie makes it easy to integrate with your existing security stack with our open API and a host of security capabilities, most of which are free.
SecOps Cloud Platform
The SecOps Cloud Platform can be used to secure and monitor organizations: endpoint capabilities, alerting from logs regardless of the source, automating response regardless of the environment.
Reducing Splunk spend
Endpoints as well as applications produce vast amounts of data. Reduce your security tooling spend by transforming, enriching, anonymizing, and routing data at the event level.
Blumira builds with LimaCharlie
Blumira found that SecOps Cloud Platform vendor LimaCharlie offered the best balance of capabilities, cost, and support as a platform on which to build a technology core to their business.